
This training is provided by Omni212 headquartered in Bellevue, WA. Omni212 is an authorized training partner for VMEdu, a global Agile & Scrum education provider. For more information, please visit:
About Scrum Developer Certified Self-Paced / On-Demand class
This is a self-paced / on-demand course. Once you register and make the payment, you will be provided access to on-demand portal with your own login. You will have access to this portal for 180 days.
You will be provided access to the online course beginning December 1, 2017. Once access is granted, you will have 180 days to take the course as many times as you wish.
Once you finish taking the course, we will help you schedule an online proctored certification exam.
This course includes:
Training manuals shipped directly to you
75 High Quality Videos
217 Terms and Definitions
16 PMI Approved PDUs
1 Illustrative Case Study
1 Crossword for Fun
3 Reference Material
Additional Benefits:
Get access to this course via Mobile App on iOS and Andrioid
Progress Tracking
Continuous Improvement
Collaborate and Learn
Scrum Brochure
http://bit.ly/2itHHT8
Sample Videos
These are just a sample showcase of videos with high quality included in this on-demand / self-paced course:
Scrum in 6 minutes video: http://bit.ly/2ysZmVR
Scrum & Agile video: http://bit.ly/2zc8mf1
Scrum mobile app video: http://bit.ly/2zesYpo
Why use Scrum video: http://bit.ly/2A6wYoP
Scrum Developer Certification exam
Once you finish taking the course, we will help you schedule an online proctored certification exam.
Training Dates
This is a self-paced / on demand course. You can take it anytime upto 180 days after you get access to the course. You can watch it as many times as you like within these 180 days.
December 1, 2017 – May 31, 2018
You will be provided access to the online course beginning December 1, 2017. Once access is granted, you will have 180 days to take the course as many times as you wish.
Scrum Developer Certified (SDC™) – Training
Scrum Developer Certification classroom trainings are offered by SCRUMstudy approved Authorized Training Partners (A.T.P.s). All trainers are highly experienced and accredited by SCRUMstudy. Participants will be awarded ‘Scrum Developer Certified’ certificate from SCRUMstudy on successful completion of the exam.
Audience Profile
This is highly recommended for everyone in a company who works in a Scrum Team or anyone who interacts with any Scrum Team. This will also be very useful for those who are interested in understanding the basics of Scrum and how this method could be used effectively.
Course Objectives and Benefits:
Objectives are:
To ensure that students understand the basics of Scrum
To enable Scrum Team members to effectively contribute to a Scrum project.
To enable Scrum Team members to apply Scrum effectively in Scrum/Agile projects.
Benefits are:
High quality hands-on training using role-plays and case-studies.
Course fee includes certification exam fee.
Complimentary copy of the SBOK™ Guide.
Free Lifetime Primary Membership.
One year Advanced Membership worth $120.
PMI approved PDUs.
Course Outline
Syllabus:
Chapter 1: Introduction
Scrum Overview
Scrum Principles
Scrum Aspects
Scrum Processes
Scrum Summary
Scrum Advantages
Chapter 2: Organization
Core Roles
o Core Role: Product Owner
o Core Role: Scrum Master
o Core Role: Scrum Team
Non-core Roles
Chapter 3: Business Justification
Responsibilities of Scrum Roles in Business Justification
Factors used to Determine Business Justification
Business Justification Evaluation Techniques
Tools for Planning Value
Continuous Value Justification
Summary of Responsibilities
Chapter 4: Quality
Quality Defined
Acceptance Criteria and the Prioritized Product Backlog
Quality Management in Scrum
Quality Planning
Continuous Integration and Sustainable Pace
Quality Control and Quality Assurance
Summary of Responsibilities
Chapter 5: Change
Unapproved and Approved Change Requests
Change in Scrum
Balancing Flexibility and Stability
Achieving Flexibility
Changes to a Sprint
Impact of Expected Change on the Length of Sprint
Managing Changes through Prioritized Product Backlog Grooming
Managing Changes During Demonstrate and Validate Sprint
Chapter 6: Risk
What is Risk?
Risks and Issues
Risk Management Procedure
Risk Identification
Risk Assessment
Risk Assessment Techniques:
Risk Mitigation
Risk Communication
Minimizing Risks through Scrum
Summary of Responsibilities
Chapter 7: Introduction to Scrum Project Phases
Chapter 8: Initiate Phase
Process 1: Create Project Vision
Process 2: Identify Scrum Master and Stakeholder(s)
Process 3: Form Scrum Team
Process 4: Develop Epic(s)
Process 5: Create Prioritized Product Backlog
Process 6: Conduct Release Planning
Chapter 9: Plan and Estimate Phase
Process 1: Create User Stories
Process 2: Approve, Estimate, and Commit User Stories
Process 3: Create Tasks
Process 4: Estimate Tasks
Process 5: Create Sprint Backlog
Chapter 10: Implement Phase
Process 1: Create Deliverables
Process 2: Conduct Daily Standup
Process 3: Groom Prioritized Product Backlog
Chapter 11: Review and Retrospect Phase
Process 1: Convene Scrum of Scrums
Process 2: Demonstrate and Validate Sprint
Process 3: Retrospect Sprint
Chapter 12: Release Phase
Process 1: Ship Deliverables
Process 2: Retrospect Project
Chapter 13: Scaling Scrum
Scalability of Scrum
Transition to Scrum
Resistance to Change
Mapping Traditional Roles to Scrum
Importance of Executive Support
Scrum Developer Certified (SDC™) – Certification exam
Scrum Developer Certified (SDC™) is an entry level certification for Scrum Team members and those who interact with any Scrum Team. The objective of this certification is to ensure that Scrum Team members know enough about Scrum to effectively contribute to a Scrum project. The courseware and preparation tools required for the certification exam will be made available on an online portal. An online proctored exam will be conducted at the end of the course.
Certification Prerequisites
There is no formal prerequisite for this certification.
Exam Format
Multiple choice
75 questions per exam
No negative marks for wrong answers
90 minutes duration
Proctored online exam
Current pass rate: 98%
Refund Policy
1. There are no refunds.
2. If for any reason the course has not been taken, class is cancelled or rescheduled, the payment can be applied towards any future course by Omni212.

2018 Print Model Casting Calls for Miss 2018 Ethnic Queen Magazine and Miss 2018 Girl 9 Magazine Worldwide Model Search
Official International Beauty Movement 2018 Ethnic Model Casting Calls for Miss 2018 Ethnic Queen Magazine Ethnic Model of the Year and Miss 2018 Girl 9 Magazine Lingerie Model of the Year model search worldwide for all gorgeous and glamorous aspiring female models ages 18-35 that would like to become Miss 2018 Ethnic Queen Magazine 2018 Ethnic Model of the Year, or would like to become Miss 2018 Girl 9 Magazine Lingerie Model of the Year and have your face on the cover as the model of the year with an exclusive full featured magazine layout of you as the model of the Year in Ethnic Queen Magazine or Girl 9 Magazine January 2018 Issue.
Are you are a gorgeous and glamorous aspiring Ethiopian female model age 18-35 with a unique beautiful look, great skin, and a great body and you have serious dreams of modeling and have always wanted to be a professional model, but you can’t find the right legit opportunity that would give you a real chance to expand your modeling career worldwide and be seen by thousands of people daily including fashion and entertainment industry insiders?
Are you seriously interested in giving your modeling career a real jump start, expanding your modeling portfolio, getting paid modeling jobs, or becoming a featured female print model in an internationally known online magazine that is known worldwide for featuring some of the most gorgeous and glamorous models worldwide?
Do you have the creative talent, the persistence, the beauty, the body, the style, and a great recent professional photo portfolio of at least 12 full body photos that are no older than 12 months, that are worthy of being featured and published in our magazine?
If you answered yes to one of the questions above and you are a serious aspiring model that has a dream of doing print modeling or professional modeling and you are looking for an incredible free opportunity to gain worldwide exposure as a print model, this is an opportunity you don’t want to miss if modeling is your passion or you have dreams of modeling, because this is a free opportunity that you should take advantage of if you are serious about jump starting your modeling career, or expanding your modeling career this year.
We will be selecting an Ethnic female Model of the Year for Miss 2018 Ethnic Queen Magazine and other ethnic female models that will also be featured with her in the January 2018 Issue of Ethnic Queen Magazine, We will also be selecting a female Lingerie Model of the Year for Miss 2018 Girl 9 Magazine and other lingerie and bikini female models that will also be featured with her in the January 2018 Issue of Girl 9 Magazine.
This is one of the 2018 fashion industry print model opportunity of the year for all aspiring and professional models that are looking for a free legitimate modeling opportunity that could take your modeling dreams to a paying modeling career level.
This is an amazing free modeling print opportunity for you to be Miss 2018 Ethnic Queen Magazine, Miss 2018 Girl 9 Magazine, or a possible feature model in the in one of these internationally known magazines, that could give you the high profile modeling opportunity that you are looking for and takes your aspiring modeling career to the next level, possibly opening doors to great paying fashion and entertainment job opportunities in the future.
If you are ready to take your aspiring modeling career to the next level as a possible magazine print model read the Model Submission guidelines Below:
Miss 2018 Ethnic Queen Magazine Model Submission Guideline:
To apply for consideration as Miss 2018 Ethnic Queen Magazine featured Ethnic model in the 2018 issue of Ethnic Queen Magazine,
YOU MUST BE AN ETHNIC FEMALE AGES 18-35 ONLY, and must be an Asian model, Indonesian model, Black model, Ethiopian model, Middle Eastern model, Latina model, Indian model, African American model, or a Bi-racial model, you will need to submit a professionally written bio letting us know which casting call you are responding to, with your age, your city, state, or country, your height, weight, measurements, your email address, and phone number and submit 12 -20 recent professional full body high resolution photos in one of the following: formal dress clothing and heels, ethnic clothing or native clothing, casual clothing and heels, or lingerie.
Please submit no less than 12 of your most recent and most impressive full body professional high resolution photos (that are no older than 12 months) with no writing on them, no logos, or photographer watermarks or signatures.
Submit 12 -20 recent full body professional photos of you posing and bio with complete contact information and measurements to: internationalbeautymovement@aol.com
All photos submitted by ethnic models will be evaluated on ethnic clothing style, creative posing, makeup and hair styling, photo shoot location, and unique ethnic look and beauty.
Miss 2018 Girl 9 Magazine Model Submission Guideline:
To apply for consideration as Miss 2018 Girl 9 Magazine featured Lingerie model in the 2018 issue of Girl 9 Magazine,
YOU MUST BE A FEMALE AGES 18-35 ONLY you will need to submit a professionally written bio letting us know which casting call you are responding to, with your age, your city, state, or country, your height, weight, measurements, your email address, and phone number and submit 12 -20 recent professional full body high resolution photos in one of the following: lingerie, bikini swimwear, or artistic nude only.
Submit 12 -20 recent full body professional photos of you posing in your hottest bikini, artistic nude, or lingerie only and bio with complete contact information and measurements to: girl9magazine@aol.com
Girl 9 Magazine is accepting photo portfolios from Asian models, Indonesian models, Ethnic models, African models, European models, Latina models, Indian models, Ethiopian models, Russian models, African American models, White models, Italian models, Bi-racial models, erotic models, exotic models, Muslim models, vixen models, artistic nude models, fitness models, bikini models, inked models, and beautiful females with fit sexy bodies that want to apply for this worldwide magazine print modeling opportunity of the year.
All photos submitted by lingerie and bikini models will be judged on skin beauty, body fitness, curves, creative sexy posing quality, and photo shoot location.
THESE PHOTO SUBMISSION GUIDELINES APPLY TO ALL OF THE ABOVE CASTING CALLS.
We do not accept photos that are older than 12 months, we do not accept less than 12 recent high resolution professional full body photos, we do not accept camera phone photos, we do not accept photos with more than one model in it, we do not accept photos posted on other websites, we do not accept low resolution photos, we do not accept comp cards, we do not accept photos with writing on them, logos, or photographer signatures, and we do not accept personal photos or photos that are taken in your home, we do not accept photos that are collages or have effects, or have borders added to them, so please do not submit none of the above photos for consideration.
Please Feel Free To Visit Our Websites and Read Our Magazines At The Links Below:
International Beauty Movement Web Site:
http://internationalbeaut.wix.com/internationalbeauty
Check Out the International Beauty Movement Magazines By Clicking Link:
http://pubhtml5.com/homepage/frnv
Click the Link Below To Sponsor or Make a Donation:
https://myevent.com/internationalbeautymovement
Click Link Below To Become a Member of the International Beauty Movement:
https://plus.google.com/communities/116221426422258310365
Please visit our casting call link to view all of our current casting calls for aspiring female models, fashion events, clothing designers, photography and video internships, makeup artists, and hair stylists worldwide at: http://rippingrunways.blogspot.com/

Next class starting
December 3, 2017
Video Conference link for the Training
Will be sent upon Registration and Payment
Why Big Data Training from Omni212?
1. Omni212 is a Hortonworks Hadoop Consulting Partner.
2. Certifed Hadoop instructors teach this class.
3. Cloud account on Microsoft Azure with Hands-on lab exercises under the guidance of two experienced big data, hadoop instructors.
4. Post class support and access to class materials on the cloud available for one year.
5. Career advancement and Job placement assistance
6. Course completion certificate available upon request.
Class Schedule
December 3 – December 14, 2017
Every week, Sun, Mon, Wed, Thu 7:00 – 9:00 PM (PACIFIC STANDARD TIME)
Training Dates
December 3,4,6,7,10,11,13,14, 2017
Pre-requisite
Desired but not required – exposure to, working proficiency of BI, sql, scripting, how to handle and manage data and databases, using Excel.
Training Session Details
There will be 8 online sessions, each session being 2 hours. Every session will have presentation about theory, concepts and technology, followed by Hands-on Lab practice exercises.
Each student will have access to a login account on the cloud, Microsoft Azure, where they can install Hadoop on a cloud virtual machine and perform hands-on lab exercises with instructor guidance. There will be two experienced big data, hadoop instructors supporting the students throughout the class.
Each session will be recorded and the recordings will be shared after each session with students.
Class recordings, training manuals and lab material will be available to students for one year after the date of completion of the course.
Course Outline
Session 1: Big Data Basics
• An Introduction to Big Data?
• Why Big Data? Why now?
• The Three Dimensions of Big Data (Three Vs)
• Evolution of Big Data
• Big Data versus Traditional RDBMS Databases
• Big Data versus Traditional BI and Analytics
• Big Data versus Traditional Storage
• Key Challenges in Big Data adoption
• Benefits of adoption of Big Data
• Introduction to Big Data Technology Stack
• Apache Hadoop Framework
• Introduction to Microsoft HDInsight – Microsoft’s Big Data Service
Hands-On Lab:
• Creating Azure Storage Account
• Creating HDInsight Cluster
• Using services on HDInsight Cluster
Session 2: The Big Data Technology Stack
• Basics of Hadoop Distributed File System (HDFS)
• Basics of Hadoop Distributed Processing (Map Reduce Jobs)
Hands-On Lab:
• Loading files to Azure storage account
• Moving files across HDInsight Cluster
• Remote Access to Azure Storage Account and HDInsight Cluster
Session 3: Deep dive into Hadoop Storage System (HDFS) (1 Hour)
• HDFS
• Reading files with HDFS
• Writing files with HDFS
• Error Handling
Hands-On Lab:
• Accessing Hadoop configuration files using HDInsight Cluster
Session 4: Processing Big Data –MapReduce and YARN
• How MapReduce works
• Handling Common Errors
• Bottlenecks with MapReduce
• How YARN (MapReduceV2) works
• Difference between MR1 and MR2
• Error Handling
Hands-On Lab:
• Running a simple MapReduce application (word count)
• Running a custom MapReduce application (census data)
• Running MapReduce via PowerShell
• Running a MapReduce application using PowerShell
• Monitoring application status
Session 5: Big Data Development Framework
• Introduction to HIVE
• Introduction to PIG
• HBase
Hands-On Lab:
• Loading the data into HIVE
• Submitting Pig jobs using HDInsight
• Submitting Pig jobs via PowerShell
Session 6: Big Data Integration and Management
• Big Data Integration using Polybase
• Big Data Management using Ambari
Hands-On Lab:
• Fetching HDInsight data into SQL
• Using Ambari for managing HDInsight cluster
Session 7: Big Data – BI and Reporting using Power BI
• Introduction to Power BI
• Usual workflow of Power BI
• Power BI Ecosystem
• Getting Data into Power BI
• Reports vs Dashboards
• Additional elements of Power BI Reports
Hands-On Lab:
• Fetching HDInsight Data into Power BI desktop
• Data Modelling using Power BI desktop
• Creating reports using Power BI desktop
Session 8: PowerBI.com services – Deep dive
• Power BI Dashboards
• Natural Language Query
• Power BI Workspaces – Personal and Group Workspaces
• Sharing using OneDrive for Business
Hands-On Lab:
• Publishing reports to Powerbi.com
• Sharing reports using OneDrive for Business
End-to-End Use Case Implementation- Lab Exercise:
• Use case -Healthcare Analytics using Hadoop framework through Microsoft HDInsight and Power BI
Class Size: Maximum 22
Price: $495
REFUND POLICY
1. There will be no refunds.
2. If a class is not taken for any reason, purchase price can be applied toward any published future class by Omni212 of equal or lesser value.
Our Big Data Consulting Projects Showcase
Learn more about our Big Data Consulting projects showcase:
Our Corporate Training Offering
Learn more about our Corporate Training offering:
STUDENT REVIEWS
AJ, Deputy CIO, City of Phoenix – Well published labs, class notes and videotaping of all classes. (evaluation score 4.9/5.0)
Henry Figueroa, Business Analyst – Great job! I cannot sign up for your upcoming hacking course and others due to another scheduled training commitment, but will consider future schedules as they come. (evaluation score 4.95/5.0
Omni212 Prime membership
Now become an Omni212 Prime member and get $100 off every training course published by Omni212 on eventbrite
Sign up for Omni212 Prime membership: http://bit.ly/2yT72Qu
To see all currently published Omni212 courses in eventbrite, type your city name and ‘Omni212’ in the evenbrite search box.
Unlimited Training
Now you can enjoy unlimited training from Omni212. Find out more about our Unlimited training Plan:
http://bit.ly/2A1L6R6
he College of Business and Economics (CoBE) of Addis Ababa University (Ethiopia) together with Jönköping International Business School (JIBS) of University of Jönköping (Sweden) is planning to host an international conference on business and economics to be held 6-8 December 2017 in Addis Ababa. To this end, CoBE invites submissions of completed but unpublished papers that focus on contemporary issues pertinent to socio-economic development of Africa. The topic areas of the papers to be submitted for the conference focus on a wide range of issues within the disciplines of management/business administration, economics, finance, public administration and development management. Both theoretical and empirical works that are within the indicated disciplines and are of relevance for Africa will be accepted. The papers might address Africa as a whole, specific region in Africa, or specific countries in the continent. Submissions from anywhere are welcomed as long as they address contemporary issues in the development and transformation of Africa. The aim of the conference is to gather leading academicians working on issues relevant to the development of Africa, policy makers, and researchers to share their knowledge, new ideas as well as to discuss future changes in the socio-economic development of Africa. The conference also aims to provide an opportunity for young researchers and practitioners to interact with senior researchers working on Africa from around the world. It will also create a special opportunity for PhD students to present their works and obtain feedback from senior scholars organizing and/or participating on the conference. Furthermore, students from the varying disciplines of business, economics, public administration and development management will have an opportunity to know what is done outside their own disciplines.

Ask us how you can save $1000 off the ticketed price
Video Conference Details
Will be sent to you once you register and make the payment
Next class starting
Devember 9, 2017
Training Session Details
There will be 10 online sessions, each session being of 2.5 hours. Every session will have presentation about theory, concepts and technology, followed by Hands-on Lab practice exercises.
Training Dates
Begins December 9, taught over 5 weekends ending Januray 7, 2018
Sat and Sun 8:00 AM – 10:30 AM (US Pacific Time)
Class dates: December 9,10,16,17,23,24,30,31,January 6,7
Each session will be recorded and the recordings will be shared after each session with students.
The Certified Ethical Hacker V9 Class
Introduction
The Certified Ethical Hacker program is the pinnacle of the most desired information security training program any information security professional will ever want to be in. To master the hacking technologies, you will need to become one, but an ethical one! The accredited course provides the advanced hacking tools and techniques used by hackers and information security professionals alike to break into an organization. As we put it, “To beat a hacker, you need to think like a hacker”. This course will immerse you into the Hacker Mindset so that you will be able to defend against future attacks. The security mindset in any organization must not be limited to the silos of a certain vendor, technologies or pieces of equipment.
This ethical hacking course puts you in the driver’s seat of a hands-on environment with a systematic process. Here, you will be exposed to an entirely different way of achieving optimal information security posture in their organization; by hacking it! You will scan, test, hack and secure your own systems. You will be taught the five phases of ethical hacking and taught how you can approach your target and succeed at breaking in every time! The five phases include Reconnaissance, Gaining Access, Enumeration, Maintaining Access, and covering your tracks!
Why EC Council Certified Ethical Hacker Class?
1. EC Council Certified Instructor teaches the class
2. Printed Training Manuals (EC Council Training kits)
3. 6 months of iLabs Activation – access to EC Council portal
4. Class recordings uploaded on the cloud after every session
5. EC Council Certification Exam Voucher
Target Audience
This course will significantly benefit security officers, auditors, security professionals, site administrators, and anyone who is concerned about the integrity of the network infrastructure.
Prerequisites
The knowledge and skills that a learner must have before attending this course is as follows:
Have successfully completed EC-Council’s Certified Network Defender (CND) course or
Have successfully completed CompTIA’s Security+ (IN-SE) course
There is a minimum age requirement that applies and attendance of the Ethical Hacking and Countermeasures training course or attempts at the relevant exam, is restricted to candidates who are at least 18 years old.
Why Certified Ethical Hacker Training from us ?
Our CEH training is very hands on. You will use Virtual images including Kali Linux image for practical lab exercises.
Our Instructors are EC Council Certified Ethical Hackers and penetration testers who actively work on helping the police and Government with cybercrimes.
Employees of Microsoft, Dept. of Homeland Security, TD Ameritrade, a Minnesota county and other companies have taken our classes.
Those with US Top Security Clearance have taken our class.
Who should take this class?
Our typical student profile is someone who wants to learn ethical hacking to enhance their cybersecurity skills, those who want to take the CEH V9 certification exam, software engineer, cybersecurity, information security professionals, IT professional, network engineer, students.
Course Objectives
Upon completing this course, the learner will be able to:
Master an ethical hacking methodology that can be used in a penetration testing or ethical hacking situation. You walk out the door with ethical hacking skills that are highly in demand, as well as the internationally recognized Certified Ethical Hacker certification! This course prepares you for EC-Council Certified Ethical Hacker exam 312-50. Cost of exam is included in the price.
Course Content
1. Introduction to Ethical Hacking
Internet is Integral Part of Business and Personal Life – What Happens Online in 60 Seconds
Information Security Overview
Information Security Threats and Attack Vectors
Hacking Concepts, Types and Phases
Ethical Hacking Concepts and Scope
Information Security Controls
Information Security Laws and Standards
2. Footprinting and Reconnaissance
Footprinting Concepts
Footprinting Methodology
Footprinting Tools
Footprinting Countermeasures
Footprinting Penetration Testing
3. Scanning Networks
Overview of Network Scanning
CEH Scanning Methodology
Scanning Beyond IDS
Banner Grabbing
Scan for Vulnerability
Draw Network Diagrams
Prepare Proxies
Scanning Pen Testing
4. Enumeration
Enumeration Concepts
NetBIOS Enumeration
SNMP Enumeration
LDAP Enumeration
NTP Enumeration
SMTP Enumeration
Enumeration Countermeasures
SMB Enumeration Countermeasures
Enumeration Pen Testing
5. System Hacking
Information at Hand Before System Hacking Stage
System Hacking: Goals
CEH Hacking Methodology (CHM)
CEH System Hacking Steps
Hiding Files
Covering Tracks
Penetration Testing
6. Malware Threats
Introduction to Malware
Trojan Concepts
Types of Trojans
Virus and Worms Concepts
Malware Reverse Engineering
Malware Detection
Countermeasures
Anti-Malware Software
Penetration Testing
7. Sniffing
Sniffing Concepts
MAC Attacks
DHCP Attacks
ARP Poisoning
Spoofing Attack
DNS Poisoning
Sniffing Tools
Sniffing Tool: Wireshark
Follow TCP Stream in Wireshark
Display Filters in Wireshark
Additional Wireshark Filters
Packet Sniffing Tool: Capsa Network Analyzer
Network Packet Analyzer
Counter measures
Sniffing Detection Techniques
Sniffing Pen Testing
8. Social Engineering
Social Engineering Concepts
Social Engineering Techniques
Impersonation on Social Networking Site
Identity Theft
Social Engineering Countermeasures
Penetration Testing
9. Denial of Service
DoS/DDoS Concepts
DoS/DDoS Attack Techniques
Botnets
DDoS Case Study
DoS/DDoS Attack Tools
Counter-measures
DoS/DDoS Protection Tools
DoS/DDoS Attack Penetration Testing
10. Session Hijacking
Session Hijacking Concepts
Application Level Session Hijacking
Network-level Session Hijacking
Session Hijacking Tools
Counter-measures
Session Hijacking Pen Testing
11. Hacking Web Servers
Webserver Concepts
Webserver Attacks
Attack Methodology
Webserver Attack Tools
Counter-measures
Patch Management
Webserver Security Tools
Webserver Pen Testing
12. Hacking Web Applications
Web App Concepts
Web App Threats
Web App Hacking Methodology
Web Application Hacking Tools
Countermeasures
Security Tools
Web App Pen Testing
13. SQL Injection
SQL Injection Concepts
Types of SQL Injection
SQL Injection Methodology
SQL Injection Tools
Evasion Techniques
Counter-measures
14. Hacking Wireless Networks
Wireless Concepts
Wireless Encryption
Wireless Threats
Wireless Hacking Methodology
Wireless Hacking Tools
Bluetooth Hacking
Counter-measures
Wireless Security Tools
Wi-Fi Pen Testing
15. Hacking Mobile Platforms
Mobile Platform Attack Vectors
Hacking Android OS
Hacking iOS
Hacking Windows Phone OS
Hacking BlackBerry
Mobile Device Management (MDM)
Mobile Security Guidelines and Tools
Mobile Pen Testing
16. Evading IDS, Firewalls and Honeypots
IDS, Firewall and Honeypot Concepts
IDS, Firewall and Honeypot System
Evading IDS
Evading Firewalls
IDS/Firewall Evading Tools
Detecting Honeypots
IDS/Firewall Evasion Counter-measures
Penetration Testing
17. Cloud Computing
Introduction to Cloud Computing
Cloud Computing Threats
Cloud Computing Attacks
Cloud Security
Cloud Security Tools
Cloud Penetration Testing
18. Cryptography
Market Survey 2014: The Year of Encryption
Case Study: Heartbleed
Case Study: Poodlebleed
Cryptography Concepts
Encryption Algorithms
Cryptography Tools
Public Key Infrastructure (PKI)
Email Encryption
Disk Encryption
Cryptography Attacks
Cryptanalysis Tools
Class Size: Maximum 22
Price: $2495
Refund Policy
1. There will be no refunds.
2. If a class is not taken for any reason, rescheduled or cancelled, purchase price can be applied toward any published future class of equal or lesser value.

Ask us how you can save $1000 off the ticketed price
Video Conference Details
Will be sent to you once you register and make the payment
Next class starting
Devember 16, 2017
Training Session Details
There will be 8 online sessions, each session being of 2.5 hours. Every session will have presentation about theory, concepts and technology, followed by Hands-on Lab practice exercises.
Training Dates
Begins December 16, taught over 5 weekends ending Januray 14, 2018
Sat and Sun 6:30 AM – 10:30 AM (US Pacific Time)
Class dates: December 16,17,23,24,30,31,January 6,7,13,14, 2018
Each session will be recorded and the recordings will be shared after each session with students.
About this course
The CHFI v9 course is the world’s most comprehensive computer hacking forensic program that delivers essential knowledge of digital forensic techniques and standard forensic tools accompanied by hands-on labs to identify intruder footprints and gather necessary evidence for its prosecution.
This training presents a methodological approach to digital forensics including searching and seizing, chain-of-custody, acquisition, preservation, analysis and reporting of digital evidence.
The CHFI sets global standards for computer forensic best practices having set a recognition amongst Fortune 500 enterprises globally.
Who should attend?
• E-Business Security professionals
• Defense and Military personnel
• Systems administrators
• T managers
• Police & law enforcement personnel
• Government agencies
• Legal professionals
• Banking, Insurance and other professionals
Prerequisites
• IT/forensics professionals with basic knowledge on IT/cyber security,
• computer forensics, and incident response
• Prior completion of CEH training would be an advantage
Course Outline
Module 1. Computer forensics in today’s world
Module 2. Computer forensics investigation process
Module 3. Understanding hard disks and file systems
Module 4. Data acquisition and Duplication
Module 5. Defeating anti-forensics Techniques
Module 6. Operating system forensics
Module 7. Network forensics
Module 8. Investigating web attacks
Module 9. Database forensic
Module 10. Cloud forensic
Module 11. Malware forensic
Module 12. Investigating email crimes
Module 13. Mobile forensic
Module 14. Forensics report writing and presentation
FAQ
What are the requirements for CHFI certification?
You must have:
Basic knowledge of IT/cyber security.
Basic knowledge of computer forensics, and incident response
And prior completion of CEH training would be an advantage
What does the kit include?
You will receive the following after enrolling for CHFI-
Official Training Delivery by EC-Council certified instructor
Official Courseware
Hands-on Labs
Mock Sessions
Exam voucher
Course Completion Certificate
What is next after CHFI?
CHFI (Computer Hacking Forensic Investigator) is an advanced level certification after which you can earn your ECIH (EC-Council Certified Incident Handler) certification and then you may move on to the expert level certification, that is, CAST 612 (Advanced Mobile Forensics and Security).
Class Size: Maximum 22
Price: $2495
Refund Policy
1. There will be no refunds.
2. If a class is not taken for any reason, rescheduled or cancelled, purchase price can be applied toward any published future class of equal or lesser value.
Video Conference Details
Will be sent after registration and payment
Course Overview
The prerequisites to learning Disruptive technologies include:
Probability
Statistics
Linear Algebra
Calculus (Differential, Multivariate)
Data Structures
Algorithms
High level Programming Language such as Python for beginners
Object Oriented Programming Language such as Java (Optional)
About this course
This course is structured according to the background and existing knowledge of the students.
The goal of this course is to learn the prerequisites quickly and move on to learn the disruptive technologies
The instructor(s) and the students together decide what they want to skip and what they want to learn based on this comprehensive course outline mentioned below. Instructor can add, edit the course outline to suit the class.
What you will learn in this course?
In this course, you’ll learn the foundational knowledge which will be useful in learning disruptive technologies.
What are the pre-requisites?
No prerequisite is required.
Some statistics, probability, computer and programming background will be helpful
Comprehensive and Detailed Course Outline
Computer Programming for those with no programming background (if required, otherwise skip to next section)
Intended for students without prior programming experience.
Basic programming-in-the-small abilities and concepts including procedural programming (methods, parameters, return, values)
Basic control structures (sequence, if/else, for loop, while loop)
File processing
Arrays
An introduction to defining objects.
Intermediate Computer Programming for those with some programming background
Concepts of data abstraction and encapsulation including stacks, queues, linked lists, binary trees, recursion, instruction to complexity and use of predefined collection classes.
Data Structures & Algorithms
Fundamental algorithms and data structures for implementation
Techniques for solving problems by programming
Linked lists, stacks, queues, directed graphs.
Trees: representations, traversals.
Searching (hashing, binary search trees, multiway trees).
Garbage collection, memory management.
Internal and external sorting
Abstract data types and structures including dictionaries, balanced trees, hash tables, priority
queues, and graphs
Sorting; asymptotic analysis; fundamental graph algorithms including graph search, shortest
path, and minimum spanning trees; concurrency and synchronization;
Foundations of Computing
Examines fundamentals of logic
Set theory, induction
Algebraic structures with applications to computing
Finite state machines
Limits of computability
Probability & Statistics
Visualizing relationships in data
Seeing relationships in data.
Making predictions based on data.
Simpson’s paradox.
Probability
Introduction to Probability.
Bayes Rule.
Correlation vs. Causation.
Estimation
Maximum Likelihood Estimation.
Mean, Median, Mode.
Standard Deviation and Variance.
Outliers and Normal Distribution.
Outliers, Quartiles.
Binomial Distribution.
Manipulating Normal Distribution.
Inference.
Confidence Intervals.
Hypothesis Testing.
Regression
Linear regression.
Correlation.
Linear algebra
Vectors
Vectors and spaces
Matrix transformations
Alternate coordinate systems (bases)
Calculus (Differential calculus, multivariate calculus)
Limits and continuity
Derivatives, Differentiations
Derivatives Applications
Equations
Training Dates
December 16, 17, 23, 24, 30, 31, 6, 7, 13, 14
Times: Every Sat & Sun 7:30 AM – 9:30 AM (Pacific Standard Time)
Each session will be recorded and the recordings will be shared after each session with students
Refund Policy
1. There are no refunds.
2. If for any reason the course has not been taken, class is cancelled or rescheduled, the payment can be applied towards any future course by Omni212.
Omni212 Prime membership
Now become an Omni212 Prime member and get $100 off every training course published by Omni212 on eventbrite
Sign up for Omni212 Prime membership: http://bit.ly/2yT72Qu
To see all currently published Omni212 courses – Omni212 training and name of your city in the search box.
Unlimited Training
Now you can enjoy unlimited training from Omni212. Find out more about our Unlimited training Plan:
http://bit.ly/2A1L6R6

Ask us how you can save $100 off the ticketed price
Video Conference Details
Will be sent to you once you register and make the payment
Next class starting
Devember 16, 2017
Training Session Details
There will be 8 online sessions, each session being of 2.5 hours. Every session will have presentation about theory, concepts and technology, followed by Hands-on Lab practice exercises.
Training Dates
Begins December 16, taught over 5 weekends ending Januray 14, 2018
Sat and Sun 6:30 AM – 10:30 AM (US Pacific Time)
Class dates: December 16,17,23,24,30,31,January 6,7,13,14, 2018
Each session will be recorded and the recordings will be shared after each session with students.
About this course
CISSP training Course (Certified Information Systems Security Professional) is the essential credential for a security professional to validate their competencies and skill set to deploy a diverse information security infrastructure for protecting the organization from potential cybersecurity hazards.
The course has been sponsored by (ISC)2, one of world’s leading non-profit organization for providing healthy aids to the field of information security. The certification qualifies a candidate to effectively create, implement and evaluate the cybersecurity tools and technologies used to facilitate the healthy transfer of information across a diverse work environment.
The CISSP has been the first credential in the field of information security to meet the stern requirements of ISO/IEC Standard 17024.
Who should attend?
The CISSP training Course is ideal for those working with the profiles of:
Security Systems Engineer
Security Consultants/Analysts
Security/Network Architect
Security Auditor/Manager
Prerequisites
The candidates must meet the following requirements before taking the CISSP training course:
Have a minimum of five years of direct full-time security professional work experience in the below-mentioned domains:
Access Control
Cryptography
Application Development Security
Operations Security
Information Security Governance and Risk Management
Legal, Regulations, Investigations and Compliance
Business Continuity and Disaster Recovery Planning
Course Outline
The CISSP CBK consists of the following eight domains:
1. Security and Risk Management (Security, Risk, Compliance, Law, Regulations, and Business Continuity)
Legal and regulatory issues
Confidentiality, integrity, and availability concepts
Security governance principles
Compliance
Professional ethics
Business continuity requirements
Personnel security policies
Threat modeling
Risk considerations
Security education, training, and awareness
Security policies, standards, procedures and guidelines
2. Asset Security (Protecting Security of Assets)
Protect privacy
Information and asset classification
Ownership (e.g. data owners, system owners)
Data security controls
Appropriate retention
Handling requirements
3. Security Engineering (Engineering and Management of Security)
Security evaluation models
Security models fundamental concepts
Security architectures, designs, and solution elements vulnerabilities
Security capabilities of information systems
Engineering processes using secure design principles
Web-based systems vulnerabilities
Mobile systems vulnerabilities
Cryptography
Embedded devices and cyber-physical systems vulnerabilities
Site and facility design secure principles
Physical security
4. Communication and Network Security
Secure network architecture design
Secure communication channels
Secure network components
Network attacks
5. Identity and Access Management (Controlling Access and Managing Identity)
Access control attacks
Physical and logical assets control
Identity as a service (e.g. cloud identity)
Identification and authentication of people and devices
Identity and access provisioning lifecycle (e.g. provisioning review)
Third-party identity services (e.g. on-premise)
6. Security Assessment and Testing (Designing, Performing, and Analyzing Security Testing)
Test outputs (e.g. automated, manual)
Security process data (e.g. management and operational controls)
Security architectures vulnerabilities
Security control testing
Assessment and test strategies
7. Security Operations (Foundational Concepts, Investigations, Incident Management, and Disaster Recovery)
Logging and monitoring activities
Investigations support and requirements
Incident management
Provisioning of resources
Foundational security operations concepts
Recovery strategies
Resource protection techniques
Physical security
Preventative measures
Patch and vulnerability management
Change management processes
Business continuity planning and exercises
Personnel safety concerns
Disaster recovery processes and plans
8. Software Development Security (Understanding, Applying, and Enforcing Software Security)
Development environment security controls
Security in the software development lifecycle
Acquired software security impact
Software security effectiveness
FAQ
What is the CISSP Certification Process?
We follow a distinct certification process for CISSP that will help you to face the challenges of the IT world. Hence, you are required to follow the below listed pointers to earn your CISSP certification –
You need to attend one complete batch of CISSP
You are then required to enroll yourself for the CISSP exam
You need to complete the CISSP exam with minimum passing score of 700 out of 1000 points
What is the value of the CISSP certification?
CISSP certification is meant for the next generation of Information Security Leaders therefore it carries immense value. It is an ideal credential for those with proven deep managerial and technical competence, experience, skills and credibility to engineer, design, manage and implement their overall information security program.
What is the intended audience for CISSP?
CISSP training and certification is fit for the following profiles –
Security Consultant
Security Manager
IT Director/Manager
Security Auditor
Security Architect
Security Analyst
Security Systems Engineer
Chief Information Security Officer
Director of Security
Network Architect
What are the career opportunities after doing CISSP?
After attaining CISSP training and certification you can work as –
Information Security Manager
Information Security Analyst
Security Consultant (Computing / Networking / Information Technology)
Senior Security Consultant
Security Architect – IT
Chief Information Security Officer
Information Security Specialist
What is the best method to study for the CISSP?
Enroll for the CISSP training and explore all the following 8 domains of the CISSP Common Body of Knowledge (CBK) to prepare and pass the CISSP exam:
Security and Risk Management
Asset Security
Security Engineering
Communications and Network Security
Identity and Access Management
Security Assessment and Testing
Security Operations
Software Development Security
What all will I get as part of the training?
You will receive the following after enrolling for CISSP training and certification –
Training Delivery
Courseware
Mock Sessions
Course Completion Certificate
Is exam fee included in the course fee?
No, CISSP certification exam fee is not included in the training cost.
What is the format of CISSP exam?
In the CISSP exam, question format of multiple choice and advanced innovative is followed.
Class Size: Maximum 22
Price: $999
Refund Policy
1. There will be no refunds.
2. If a class is not taken for any reason, rescheduled or cancelled, purchase price can be applied toward any published future class of equal or lesser value.

Video Conference Details
Will be sent after registration and payment
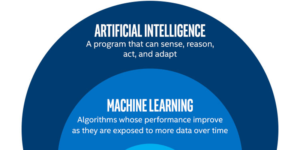
Artificial Intelligence Training
Course Overview
In this course you will learn the fundamentals of Artificial Intelligence (AI), and apply them. Design intelligent agents to solve real-world problems including, search, games, machine learning, logic, and constraint satisfaction problems.
About this course
What do self-driving cars, face recognition, web search, industrial robots, missile guidance, and tumor detection have in common? They are all complex real world problems being solved with applications of intelligence (AI). This course will provide a broad understanding of the basic techniques for building intelligent computer systems and an understanding of how AI is applied to problems.
What you will learn in this course?
In this course, you’ll learn the basics of modern AI as well as some of the representative applications of AI. Along the way, we also hope to excite you about the numerous applications and huge possibilities in the field of AI, which continues to expand human capability beyond our imagination. Learn the fundamentals of Artificial Intelligence (AI), and apply them.
What are the pre-requisites?
Linear Algebra, Probability and Statistics, Data Structures & Algorithms, Truth, deduction, and Computation, Database Systems, Logic Programming.
Course Outline
Fundamentals of AI
Statistics, Uncertainty, and Bayes networks.
Principles and programming techniques of artificial intelligence – symbol manipulation, knowledge representation, logical and probabilistic reasoning, learning, language understanding, vision, expert systems
Principal ideas and developments in artificial intelligence – Problem solving and search, game playing, knowledge representation and reasoning, uncertainty, machine learning, natural language processing
Machine learning.
Logic and planning.
Applications of AI
Image processing and computer vision.
Natural language processing and information retrieval.
Data aspect of AI, classification, clustering, normalization
Intelligent agents, uninformed search
Distance metrics (result set comparisons), grouping the results (K-means)
Heuristic search, A* algorithm
Adversarial search, games
Constraint Satisfaction Problems
Trained algorithms, e.g. random walk, hill climbing
Machine Learning: Basic concepts, linear models, perceptron, K nearest neighbors
Machine Learning: advanced models, neural networks, SVMs, decision trees and unsupervised learning
Machine learning libraries in Python
Markov decision processes and reinforcement learning
Logical Agent, propositional logic and first order logic
AI applications (NLP)
NLP libraries, e.g. nltk
AI applications (Vision/Robotics)
Expert Systems
Review and Conclusion
Training Dates
December 18, 20, 27, Jan 1, 3, 8, 10, 15, 17
Times: Every Mon & Wed 7:00 PM – 9:00 PM (Pacific Standard Time)
Each session will be recorded and the recordings will be shared after each session with students
Refund Policy
1. There are no refunds.
2. If for any reason the course has not been taken, class is cancelled or rescheduled, the payment can be applied towards any future course by Omni212.
Omni212 Prime membership
Now become an Omni212 Prime member and get $100 off every training course published by Omni212 on eventbrite
Sign up for Omni212 Prime membership: http://bit.ly/2yT72Qu
To see all currently published Omni212 courses – Omni212 training and name of your city in the search box.
Unlimited Training
Now you can enjoy unlimited training from Omni212. Find out more about our Unlimited training Plan:
http://bit.ly/2A1L6R6

EHPSA ON THIS YEAR AS A PLAN!!!
Inter professional Collaboration
Inter professional collaboration in its simplest form is the practice of approaching work from a team-based perspective, where the team consists of health care professionals from different fields, as well as other practitioners, communities and even patients.
Growing a collaborative approach between multiple parties and disciplines can lead to highly effective work outcomes as well as an increased knowledge base for everyone. The transfer of knowledge and involvement of others leads to better results and better patient care because of the wholesome insight into the issues tackled.
Action for Anticipation :
Recruit (create a plan for their involvement and how the two parties can benefit each other) students from other relevant study fields to aid the EHPSA in positions that could benefit from interdisciplinary approaches (economy, media,…):
Keys of success:
1.Number of active non-medical and medical (health) students in the EHPSA activities
2.Number of non-medical (health) and medical students who have expressed interest in getting involved in EHPSA activities
3.Number of non-medical students(Health) and medical who have attended International or National events (SRTs, Workshops, Meetings,…)

This The Mother, Baby and Child Show is expected to be the largest and unique in its nature than other expos conducted in our country that will bringing together manufacturers and retailers from the mother and baby care industry. This exciting, three days event combines an exhibition marketplace and meeting space with a focus on family.
From small innovative companies and chains, the latest technological innovations to the biggest international brands, The Mother, Baby and Child Show offers a unique and interactive opportunity for exhibitors to meet new customers face to face, drive sales, increase market share and increase family interaction.
This exhibition will be very popular among professionals and young parents, who can learn here about the novelties and innovative products and here one also can find a broad range of baby food as well as products for nursing and pregnant mothers: from special linen to outgoing dresses – everything that helps woman to be beauty, self-confident, able to lead an active life.
And also, in this expo we will arrange a conference that incorporates concerned people from government organizations, NGOs, public firms and individual professionals and there will be open panel discussion on the mother and baby care and other related industries by presenting impact assessment papers on the current activities on the necessary industry as well as other concerned parties.

Addis Digital Marketing Expo and Conference is the first digital marketing event in Ethiopia has three main sub events that are Training, Confrence and Expo. The target goup of the events are export companies , financial institutions , ICT companies , hotels and other integrated international business companies. The event will be held from February 20 – 22 at Intercontinental Addis Hotel which is a five star hotel with a big venue.

ROCK WALL WINE CO PRESENTS: LIVE MUSIC!
Rock Wall Wine Co Presents: Live Music! – Rock Wall Wines – Fri Feb 23 at 4:00PM
The James Brothers live in the Rock Wall Dome
Alameda CA – http://www.rockwallwines.com/
source categories: Wine,Food,Community
event syndication by Syndical.com
from Account: syn-rockwallwines

Vendors Trading Masses are
Global trading events held in and throughout citeis and countries worldwide it is where b2b vendors & merchants gather
together in a mass of selling power & trading power promoting their goods to
consumers,visitors,tourist and business travelers.There would be many different b2b vendor trade zones of exchange,trade events,displays,awareness,
mission gatherings and expansions combined into one forming a new city within a city filled with many vendor membership groups of all kinds of goods &
industries the ticket sales, funds, and commissions from these zones would provide new innovations and opportunities for those in need such as
social entrepreneurship for the poor,jobless, education & healthcare for the sick,needy
and housing/shelter/safehavens for those who seek refuge,security,peace, and one with God.
Events will be held simultaneously in multiple cities and spread throughout the regions of countries
under the direction of local organizers.These meeting facility events held inside/outside hotels and resorts will show off product innovations,local, and international project developments
from vendors,industries,and community projects being developed in in their city/country.To attend ,participate,and become a member of these meeting facility events.
The International Conference on Re-Emerging Infectious Diseases, organized by the Virology Education B.V. will take place from 12th March to 14th March 2018 in Addis Ababa, Ethiopia. The conference is a global platform that will bring together experts from around the world involved in emerging diseases in an interactive conference setting.
The HortiFlora Expo is believed to be an instrument to attract new investors to Ethiopia and Promote members’ product to the world. To date, many of the local and international producers, input suppliers, consultants, buyers and other pertinent stakeholders registered and secured space to get together.
At the very moment, international investors, entrepreneurs, manufacturers, dealers, and technology providers are navigating for higher potential sectors, innovative companies, entrepreneurs, and emerging partners in the domestic value chains, which is also true in the reverse. We strongly believe that African Business and Investment Expo will link the ideal partners in production, service and management, holistically, at one place.Over 200 multinational companies are expected to exhibit and have expressed interest in the African market at this highly expected EXPO. Other investment facilitating institutions have also projected opportunities in this upcoming event. The Ozzie Group is committed and prepared to bring Potential Investors and New Business Opportunity to the Exhibitors.We highly believe such breakthrough EXPOwill fast pace the next level of business activities and boost Africa’s transformation success story,bridging the demand and supply in global investment arena.
The International Conference on Occupational Science, organized by the Research Society will take place on 11th April 2018 at the Ambassador Hotel, Addis Ababa, Ethiopia in Addis Ababa, Ethiopia. The conference will provide an opportunity for academicians and professionals from various educational fields with cross-disciplinary interests to bridge the knowledge gap, promote research esteem and the evolution of pedagogy.


